Manage the security log
Learn about the what the security log tracks, and how to activate, view, and clear it.
Overview
-
The security log tracks when a user accesses areas of the system protected with security. It does not track any changes made by the user.
-
The security log can be useful to see who attempted to look at sensitive records (such as deaccessioned objects), or when the user ran a process (such as Bulk Move).
-
To see changes made by a user, use the Audit tool.
Activate the security log
-
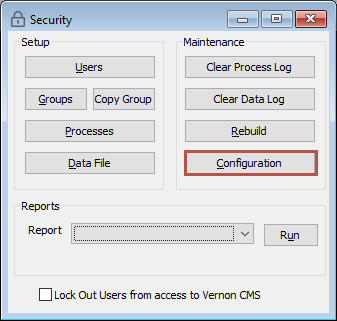
Go to Tools > System Maintenance > Security Tool.
-
Click Configuration.
-
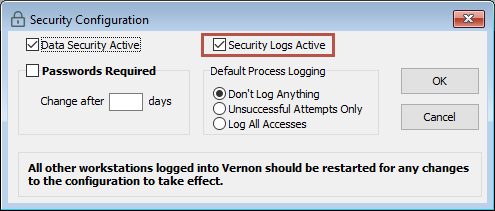
In the Security Configuration window, tick Security Logs Active.
-
For process security you can also select:
-
Don't Log Anything: Security logs will only record access to datafiles, not processes.
-
Unsuccessful Attempts Only: Security logs will only record failed attempts to access a process.
-
Log All Accesses: Security logs will record all successful and unsuccessful attempts to access a process.
-
-
Click OK. Vernon CMS will need to be restarted on other computers before the changes will take effect.
View the security log
-
Go to Tools > System Maintenance > Security Tool.
-
Under Reports, select the report type:
-
Process log: This report shows all of the users who accessed a process and the time and duration of that access.
-
Data log: This report shows all of the users who accessed records in a datafile and the time and date of access.
-
Clear the security log
You should regularly clear the security log so that the stored access records do not accumulate and take up unnecessary disk space.
Clearing the security log deletes any records stored in the log since the last time it was cleared.
-
Go to Tools > System Maintenance > Security Tool.
-
Click Clear Data Log and then click Yes.
-
Click Clear Process Log and then click Yes.
